WLS 3.5 is here! Aside from the continual improvements to the core, here are a few highlights for this release.
File Tailing
This long requested feature was finally incorporated, primarily to support PowerShell v5 history and IIS logs, but should work well for a wide variety of logs. An example configuration for PowerShell v5 and IIS is included in the recommended configuration.
PE File Information
If specified, when encountered, ImpHash and the header fields defined below are now available for PE files. For non-PE files the Signature will be logged.
PE File
Example PE file with ImpHash and the compile/link time (TimeDateStamp):
[host] Security: LogType=”WLS”, BaseFileName=”charmap.exe”, Channel=”Security”, CommandLine=”‘C:\WINDOWS\system32\charmap.exe'”, CompanyName=”Microsoft Corporation”, Computer=”[host].[domain]”, CreatorProcessName=”explorer”, EventID=”4688″, EventRecordID=”44735942″, ExecutionProcessID=”4″, ExecutionThreadID=”8992″, FileDescription=”Character Map”, FileVersion=”5.2.3668.0″, ImpHash=”7831775B376A2587FCB1CCB3E1EE37BF”, InternalName=”charmap.exe”, …, TimeDateStamp=”10/30/2015 2:37:15 AM”, TokenElevationType=”TokenElevationTypeDefault (1)”, ValidSignatureDate=”True”, Version=”2″, WindowStation=”Winsta0\Default”, Zone=”0″
Non-PE File
Example of a non-PE (16-bit!) file present in Windows 10 64-bit:
[host] WLS_FileData: LogType=”WLS”, BaseFileName=”compobj.dll”, …, SHA1=”2BE21636F3C2899F1217C289351B106118A5E197″, Signature=”NE”, WLSKey=”3012″
Additions
- CommandMonitor default support for netsh.exe and nslookup.exe
- DecodeClientAddress
- Logs with the ClientAddress field can be decoded to their actual values (IP, Port, and Scope)
- DriveMonitor
- Added DriveLogInterval to log drive details at regular intervals
- ExistingProcess
- Added the fields SubjectUserSid, SubjectUserDomain, and SubjectUserName
- FileMetadata
- CatHash available for PE files
- File header fields available for PE files
- IgnoredList option to prevent specific files from having metadata collected
- ImpHash available for PE files
- FileTail
- Monitor flat files
- Filters
- Support for wildcard characters
- Heartbeat
- Reports LogsSent
- LogRouting
- CSV output
- LogsSent is reported per-destination
- LogRouting\Servers
- SDID can be set per-server
- UTC available via the UseUTC option
- RegistryMonitor
- Filtering by key Name and Value
- PortMonitor
- Added ResolveRemoteHostName option
- SessionMonitor
- Added SecurityUserID and Certificate fields
Changes
- FileData
- Internal logs can be routed through FileData to collect file metadata based on file names contain in logs
- FileMetadata
- Errors countered during metadata collection are now reported
- FileMonitor
- Delete events now report BaseFileName
- PortMonitor
- Removed port summarization
- SSDeep (fuzzy hash)
- Calculation was replaced. Now supports incremental hashing!
Fixes
- CertificateMonitor
- Certificates with invalid public key algorithms were not reported
- CommandMonitor
- Certain errors caused commands to not be reported
- File permissions issues
- FileMetadata
- SSDeep was not calculated properly for some files
- Filtering
- The NewHash field wasn’t available to use in a filter
- Heartbeat
- Setting the interval to 0 did not disable the heartbeat
- RegistryMonitor
- Invalid registry paths would invalidate the entire group
- ReplaceProviderString
- Replacement strings containing multiple values with a comma delimiter were not replaced
- SessionMonitor
- SessionUser was not set to the actual session user when an invalid user was initially presented
- Tags
- All fields were not available to use for tagging
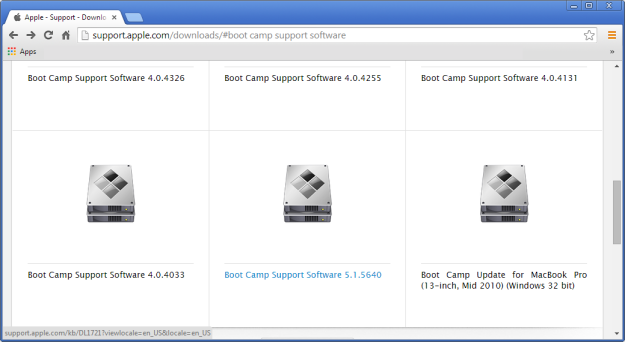
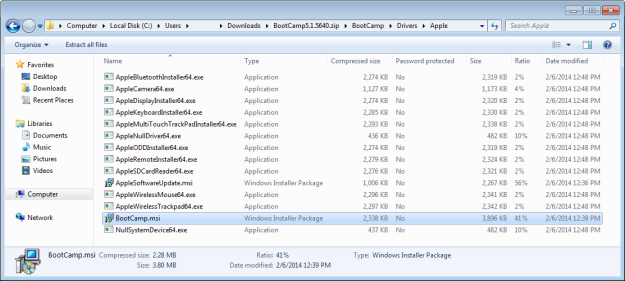
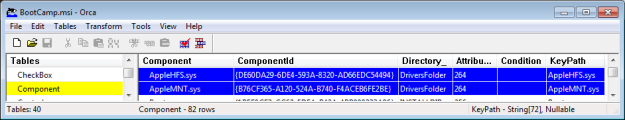
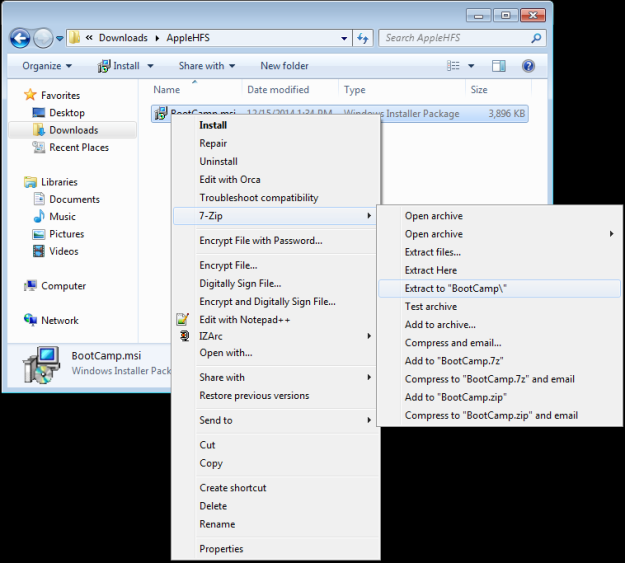
For more information on WLS, click “WLS Information” at the top, or here: WLS Information
If you’d like licensing or other information about WLS, send me a note via the contact form. WLS is currently available to US entities, but does require a signed license agreement.